For those who may have wondered, yes I am still alive.
For background there has been a decision made by VMware recently where a lot of our Non-EUC solutions include a VMware Identity Manager licensing entitlement. What this is meant to allow is something like VMware Log Insight to be able to authenticate with Identity Manager allowing simplified SSO for administrators. This entitlement to Identity Manager is for the On-Premises version only.
So now, let’s go into this scenario posed to me recently. What if that customer already has an entitlement to a SaaS Identity Manager tenant? Do they need both? Without opening a can of worms and entering the realms of licensing, the answer is “probably” and it’s actually not a bad thing. Their situation was that they had some users who needed access to Log Insight that had an entitlement to a Workspace ONE SaaS license but not all of them. This meant we had to leave Log Insight federated with the On-Premises Identity Manager. If there is where we stopped everything would have worked, but the user experience would be pretty ordinary as they’d need to authenticate to both Identity Managers.
That’s not how we roll at VMware! Lets make it simple!
For ease of explanation, let me declare a few variables refer to each of the environments as the following:
SaaS vIDM – This is the entitlement that some users have. The customer wants to put an App in their Unified Catalog so that Log Insight administrators can easily access it without having to re-authenticate.
On-Premises vIDM – This is the On-Premises vIDM that we installed purely for authenticating Log Insight (initially).
The assumption here is that you’ve got your users synced from the same Active Directory. Their details need to be the same in both environments.
And of course, you all should know what an IDP and SP is!
At a very high level, all we need to do is is make the SaaS vIDM a 3rd Party IDP in the On-Premises vIDM. Then we just need to add the On-Premises vIDM as an Application (SP) (with a few additions which I’ll explain later) in the SaaS vIDM Environment.
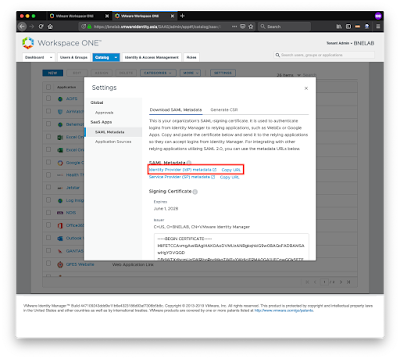
Firstly, go to your SaaS vIDM and grab your idp.xml metadata from the Admin Portal (Catalog -> Web Apps -> SAML Metadata -> Identity Provider Metadata…) and copy the URL.
This will be https://your_fqdn/SAAS/API/1.0/GET/metadata/idp.xml
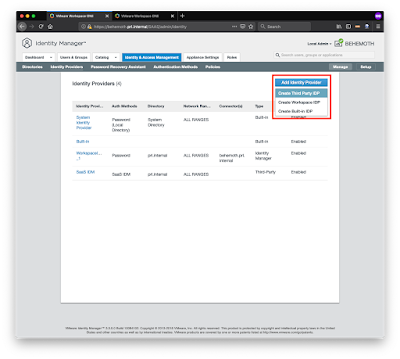
Go to your On-Premises vIDM Admin Portal and add a new 3rd Party IDP (Identity & Access Management -> Identity Providers -> Add Identity Manager -> Create Third Party IDP)
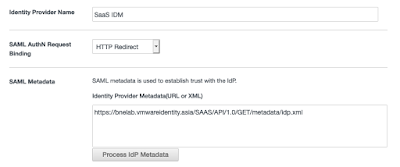
Give the IDP a name, and paste the IDP Metadata URL into the required field and select the Process iDP Metadata Button.
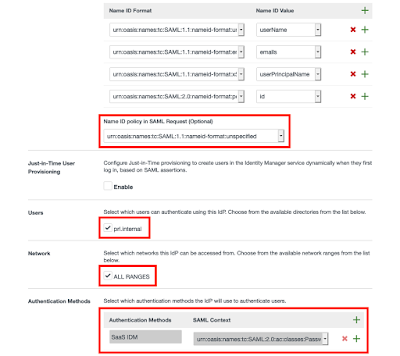
This will fill out all the required NameID Format Mapping details, but you need to make sure you change the following fields:
- Set your Name ID Policy
- Make sure you assign this to your User Directory
- Assign it to which networks you want this IDP to be available from
- Set a name for the IDP Auth Method and give it the SAML Context
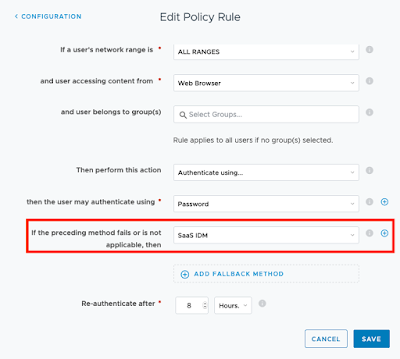
We then need to add this 3rd Party IDP as an Auth Method to whatever Access Policy is appropriate. From my testing, all that was required was having the SaaS IDP (from the previous step) as a fallback in the Access Policy.
Now we need to add the On-Prem vIDM as an App. The easiest way is to grab the sp.xml metadata from your On-Premises vIDM from the same place we got our idp.xml (obviously a different enviroment, but same relative location).
For ease it will be https://your_fqdn/SAAS/API/1.0/GET/metadata/sp.xml
Now in your SaaS vIDM Admin portal go to Catalog -> New
Give your new App a Name and Icon (if you want).
Then in the Configuration page, paste the sp.xml URL (or if that fails copy and paste the contents of the entire sp.xml) and proceed (next, next, save, assign etc.)
If we leave it at that, we’ll successfully be able to log into the SaaS Identity Manager, click on the Log Insight icon, and we’ll be taken to the On-Premises vIDM App Portal. Then we could open then Log Insight federated app and we’ll end up here!
But like I said thats still not enough of a great experience. I don’t want to have to press the LOGIN VIA SSO button.
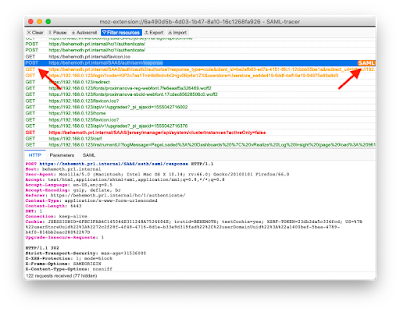
What we need to go is grab add a relay state (to both vIDMs) so that it takes us directly into the Log Insight interface. I found this by opening up my trusty SAML tracer Firefox Add-On and intercepting the SAML Assertion.
Open SAML Tracer and then go to your Log Insight URL. Press the LOGIN VIA SSO button and look at the assertion.
Look for the POST line that is the SAML response from the IDP:
Make sure you’re on the HTTP tab, and look for a line that says ‘Location’.
Copy the entire URL in Location. This is our Relay State in Identity Manager.
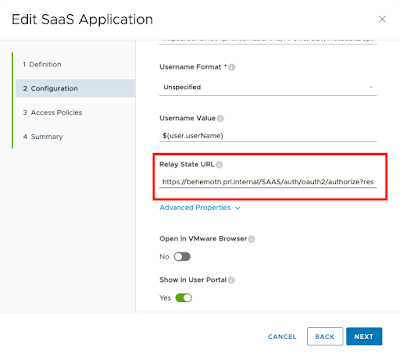
Go into your Log Insight SAML App in Identity Manager (both environments in our case) and add that ‘Location’ value as the Relay State.
We’re done. Here’s what it looks like if you’re interested.




Leave a Reply