Managing  user accounts and identities is pretty a pretty tedious task.
user accounts and identities is pretty a pretty tedious task.
One of the biggest benefits we talk about with Single Sign On and SAML authentication is the
ability Airwatch Workspace ONE UEM etc.) a user account needs to exist in that service for the user to sign in to.
to federate services to Identity Manager, but in order for a user to be able to sign into those services (Salesforce,
With any Identity Provider – Identity Manager, Azure AD, Google IDP etc. – typically those user accounts are synchronised with an On-Premises directory. If you’re not synchronising those from another directory using some form of sync tool, you are manually creating those either via bulk upload, or even worse, manually typing them in.
The same requirement exists when you’re using a cloud service. A user cannot log in with an account. Something somewhere is the source of truth of all user’s identities, but having multiple sync tools out there syncing user accounts is not great. Wouldn’t it be great if there was an easier way?
This is where Just-In-Time (JIT) provisioning comes in.
With JIT, user accounts are created on the fly the first time the user logs on to the application/service. JIT account creation extends the typical SAML authentication flow by creating the user account at the service by using the attributes passed in the SAML assertion. Its actually pretty simple.
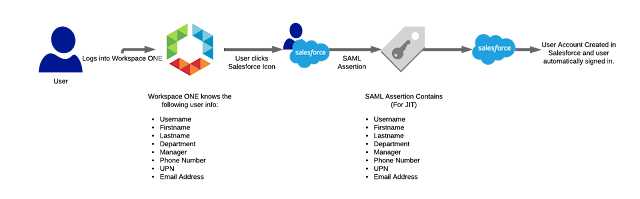
The steps are really straight forward:
- The user logs in to Workspace ONE Identity Manager.
- Our user can log in because Identity Manager already has all the user metadata as its being synced from AD/LDAP.
- They want to access Salesforce so they click on the Salesforce icon.
- A SAML assertion is generated to be sent to Salesforce, but because we’re using JIT we make sure we add all the information needed to create the user object at the Salesforce end.
- When Salesforce gets the assertion, it checks all the security and validation steps, then creates the user account with the information supplied in the assertion.



Leave a Reply