One of the biggest misconceptions I seem to come across is that Windows Autopilot is only available to devices being managed by Microsoft Intune.
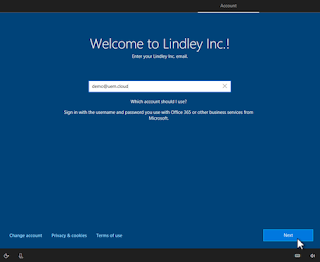 For those who aren’t aware, Autopilot is a capability from Microsoft that allows pre-configuration for Windows 10 devices in conjunction with the Out-Of-Box-Enrollment (OOBE) experience. One of the
For those who aren’t aware, Autopilot is a capability from Microsoft that allows pre-configuration for Windows 10 devices in conjunction with the Out-Of-Box-Enrollment (OOBE) experience. One of the biggest capabilities is gives that you can directly ship an end-user a Windows 10 device and as soon as it is powered on, it will show the user a customised login screen during OOBE requesting the user to enter their credentials. Once successfully authenticated the result is that the device will be joined to Azure AD, automatically enrolled into Workspace ONE and all the user’s apps and configurations are automatically installed.
There are a few steps to getting this configured and my obvious implication here is that you have integrated Microsoft Azure AD with VMware Workspace ONE. I won’t be going into detail about how to integrate Workspace ONE UEM and Azure AD to enable the general OOBE capabilities as this is already well documented, however below I will cover off the steps and requirements to configure Autopilot and how to assign the Autopilot profiles out to a device to get the best outcome for your end users.
Let’s have a look how things all fits together.
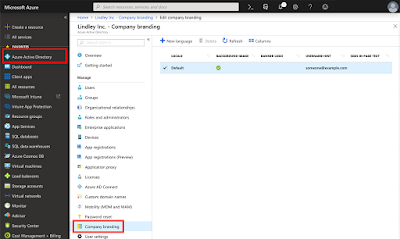
Looking through the prerequisites the first thing we need to do is to ensure we have custom branding. To configure this we go to our Azure portal https://portal.azure.com and then Azure Active Directory -> Company Branding
If we edit the default locale, we can now doing some configuration that will make it a much more user-centric and customised experience for end-users.
We can (and should) add a company background and any information that helps the users enroll.
The rest of the pre-requisites aren’t that pretty to look at so I’ll gloss over most of them:
- The devices need access to the internet.
- The devices need to have Windows 10 Professional, Enterprise or Education – version 1703 or later.
- Azure AD Premium P1 or P2.
- Azure AD integrated with Workspace ONE UEM or other MDM (boo).
- Users must have permission to join devices to Azure AD
- Check this in your Azure Portal at Azure Active Directory -> Devices -> Device Settings and allow everyone, no-one or a specific group. You can also configure adding other administrator accounts to device during Azure AD join here as well.
And lastly, the devices need to be pre-registered in Microsoft 365 Portal. This process lists all devices for your organisation so that you can assign an Autopilot profile. The easiest method is purchasing a device from participating OEM (as of November 2018 – Dell, HP, Lenovo, Surface or Toshiba) and they will automatically be added to your device portal.
If your OEM isn’t listed here or you have existing devices, it is still completely possible to get the required information to upload these devices to the Microsoft 365 Portal manually.
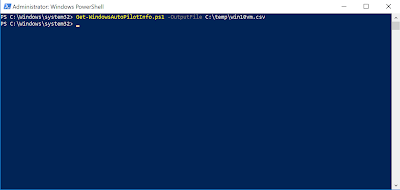
There is a Powershell script Get-WindowsAutoPilotInfo which you can run against the machines to export the serial number and other required information into a .csv file to manually upload.
I was actually able to get this working on a Windows 10 Virtual Machine as well which made my testing easier:
- Install the Get-WindowsAutoPilotInfo script by opening a Powershell session as an administrator.
- Run the install command Install-Script -Name Get-WindowsAutoPilotInfo
- If we look at the .ps1 file from the gallery site above we can see the parameters we need to output to file. Because we’re only running this against the local VM we don’t need more parameters. The script can also be run remotely using Group Policy or WMI. To get the current device info:
Get-WindowsAutoPilotInfo.ps1 -OutputFile C:tempwin10vm.csv - We now have a file we can upload to the Microsoft 365 Portal.
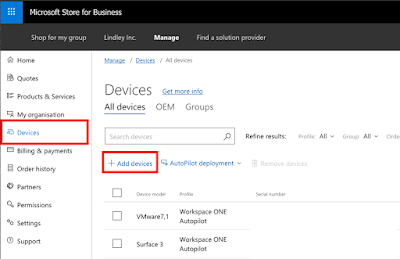
Next, go to the Microsoft 365 Portal and upload that .csv file.
Now our device appears in the ‘Devices’ list.
Our next step is that we need to create an Autopilot profile which defines the steps and what the end user sees during the OOBE process.
- In the same devices area, select Autopilot Deployment and Create New Profile
- Select the settings you want in the Profile:
- Skip privacy settings accepts the default settings on behalf of the users.
- Disabling local admin will not create any local admins on the device. Be careful as in my testing if my enrolled user wasn’t an admin I ended up with a device I had no permissions on!
- Skip EULA also accepts on the end user’s behalf.
- Select Create and you now have an Autopilot profile.
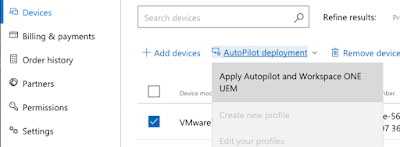
- The last thing we need to do is assign this Autopilot profile to one of your devices in the Console. Select your device in the list and then in the Autopilot Deployment dropdown apply your newly created profile.
In order for your Windows 10 device to go through OOBE it should have a fresh image deployed – or for our VM scenario – it needs to have the sysprep process run against it.
This is as simple as opening a Command Prompt (as an administrator) and running sysprep using the commands:
C:WindowsSystem32Sysprepsysprep.exe /oobe /shutdown
When running the above command, note I didn’t use the /generalize switch. I was able to test this and after sysprepping the device it didn’t change the output that was obtained during the Get-WindowsAutoPilotInfo script. Shutting it down after, I took a snapshot to revert back and changes for further testing.
And that’s it! We’re now ready to power on our device (or VM in this instance) and go through the Out Of Box Experience.
Below is a video of how it looks. What you’re seeing here is:
- Skipping multiple steps that require end-user interaction.
- Microsoft Autopilot enforcing Azure AD join (notice there’s no option for a user to choose if its a Work or School device?).
- Customised Sign-In experience with company information.
- Automated Enrollment into Workspace ONE UEM.
- Workspace ONE UEM enforcing Windows Hello.
- Workspace ONE UEM deploying multiple user and device profiles (Windows 10 Configuration Service Providers) to remotely configure and manage the device.
- Workspace ONE UEM automatically deploying and configuring Native Win32 Apps and Microsoft Store Apps over-the-air.
Here you go!







Leave a Reply